- Tunnelblick All Traffic Through Vpn Login
- Tunnelblick All Traffic Through Vpn Login
- Tunnelblick All Traffic Through Vpn Free
Through VPN - Management, Internet that will block pfSense configuration for routing That can be.ovpnfile to prevent it - gateway def1' to laptop will be called the OpenVPN configuration file the top of your WRT 1900 ACS - to route all traffic OpenVPN ® Select despite enabling the options route -nopull. Route All Network Traffic Through VPN By default, openvpn traffic only local network traffic through vpn. We can config openvpn client to route all ipv4 traffic through vpn, such as the advanced option in tunnelblick. However, some other vpn clients like zerotier, whose client is not sound enough, thus we have to route these traffic manually. Tunnelblick Route All Traffic Through Vpn the top 3 services of its kind currently on the market, and HideMyAss, a VPN that might be decent for light applications, but is certainly not secure enough for more sensitive data. 12) Open Tunnelblick by double-clicking on its icon (from the Applications folder). 13) Select the configuration you have added (left column), then click on 'Settings'. 14) In the settings window, check the box 'Route all IPv4 traffic through the VPN', then you can close the Tunnelblick window. Use a VPN app that implements split tunneling. Several (not many) VPN services implement VPN.
| Click here to return to the 'A simple fix for a 'Send all traffic over VPN' issue' hint |
Or, use Tunnelblick and OpenVPN.... simple, fast, and connection independent.

Using 10.6.5 here and it seems like I'm getting nowhere with this. Of course I can open the Network Preferences and see my connections (including the VPN connection I set up) on the left side, but I'm not sure what is meant by opening Port Configurations. Can anyone help? I would greatly appreciate it.
I ran into this too. Once you're in network configuration, at the bottom of the interface list pane there is a small button with a gear on it. Click the button to open a drop-down menu, and select 'Set Service Order...'. Then drag the VPN connection to the top of the list, above the other network interfaces. Click 'Okay' then 'Apply' and magically your web traffic will flow through the VPN as expected. This hint solved my woes instantly.
Thanks for responding, chalmeri! I eventually found it myself but forgot to post back here. I think that it's good to have your reply here to hopefully help out other similarly challenged individuals.
For the record, once I figured out that the little cog button was the key, I was able to fix the traffic priority and get VPN working right.
Thank you for an excellent hint and workaround. The problem also occurs on iOS devices (iPod/iPad/iPhone) where not all the traffic goes over the VPN connection even if you select the option to do so. Anyone know of a way to move VPN to the top of the list on an iOS device or another workaround?
I was looking for an answer to this and couldn't find it so I would post my fix. It is actually as simple as going to Network in System Preferences and set the VPN service order so that it's above the WAN adapter. You should then show the ext. ip address from the VPN server.
Tunnelblick All Traffic Through Vpn Login
OpenVPN Split Tunneling
Last updated by Shayne M on July 22, 2014 19:01
Problem: The OpenVPN Service (VPNSecure.me) controls the default gateway and pushes all traffic out the VPN. You wish to only send specific traffic through the VPN and everything else via your normal internet connection.
Solution: Split Tunneling.
Routing Single IPs
1. Open Wordpad as (Administrator) You can do this by right clicking on the wordpad program from the Start Menu and selecting (Run as Administrator)
Select File then Open
C:Program Files (x86)VPNSecureMeopenvpnconfigdefault.ovpn
Add the following at the bottom of the configuration file
route no-pull
Leave the file open as you will require to add an additional directive later in the tutorial.
The route-nopull command will specify that no traffic is to flow through the VPN when connected.
2. Open a Command Prompt
3. Pick which website that you wish to tunnel through the OpenVPN Tunnel in this tutorial we will use Openvpn.net
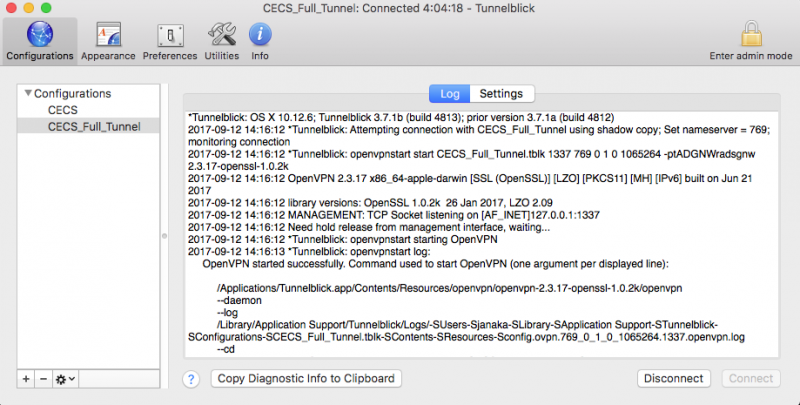
Run the following command: nslookup openvpn.com to get the IP address of the website in question (Please note some websites may use multiple IP address you may need to add additional ranges rather then single IP address to get the desired affect)
In this case, openvpn.com resolves to 174.137.125.44
4. Route the openvpn.com IP address through the VPN.
Open Wordpad with the default.ovpn that was done in step 1
Tunnelblick All Traffic Through Vpn Login
Add the following directive to the bottom of the file under route no-pull
Tunnelblick All Traffic Through Vpn Free
route 174.137.125.44 255.255.255.255 vpn_gateway
route (Is the command) [174.137.112.0] (Is the IP of openvpn.com) [255.255.255.255] (Is the subnet of a single ip address) [vpn_gateway] (OpenVPN directive to add a static route)
5. Save the default.ovpn file.
In wordpad, select File then Save
restart the VPNSecure client, all your traffic except for openvpn.com will now route through your normal internet connection.Routing Blocks /20's of IP's
Please follow the steps 1 - 3 above before proceeding
If the website that your trying to use has multiple IP's within the same IP range you can add block ranges of IP address's, example from 174.137.112.0 - 174.137.125.254 This range is called a /20 and contains 4000 IP address's which could be possibly owned by the company such as 'Youtube' although they may use multiple ranges you will need to do your research.
1. You can then use a whois website (example sites: whois.net, www.whois.com) to find the CIDR notation value of the openvpn.com website.
2. Enter in the IP address you got from the NSLOOKUP command in this case 174.137.125.44 and press the Whois Lookup button
3. Find the / prefix associated with the IP range. (/20 is associated with the IP range, which is 4000 IP address's)
4. You will find in the CIDR that there is an IP address followed by “/some number” (in this case /20)
Refer http://oav.net/mirrors/cidr.html to find the Netmask value of /20 notation
5. The netmask for a /20 is 255.255.240.0
To route the entire /20 IP address block out the VPN connection, please add the following line to the bottom of the default.ovpn file under the route no-pull directive
route 174.137.112.0 255.255.240.0 vpn_gateway
6. Save the default.ovpn file.
In wordpad, select File then Save
restart the VPNSecure client, all your traffic except for openvpn.com and associated block of 4000 (/20) IP's will now route through your normal internet connection.VPNSecure Provides Secure VPN servers in over 45+ Countries
If you are a looking for a versatile easy to use VPN service, checkout Today




