- Easily connect Okta with Cisco ASA VPN (SAML) or use any of our other 6,500+ pre-built integrations.
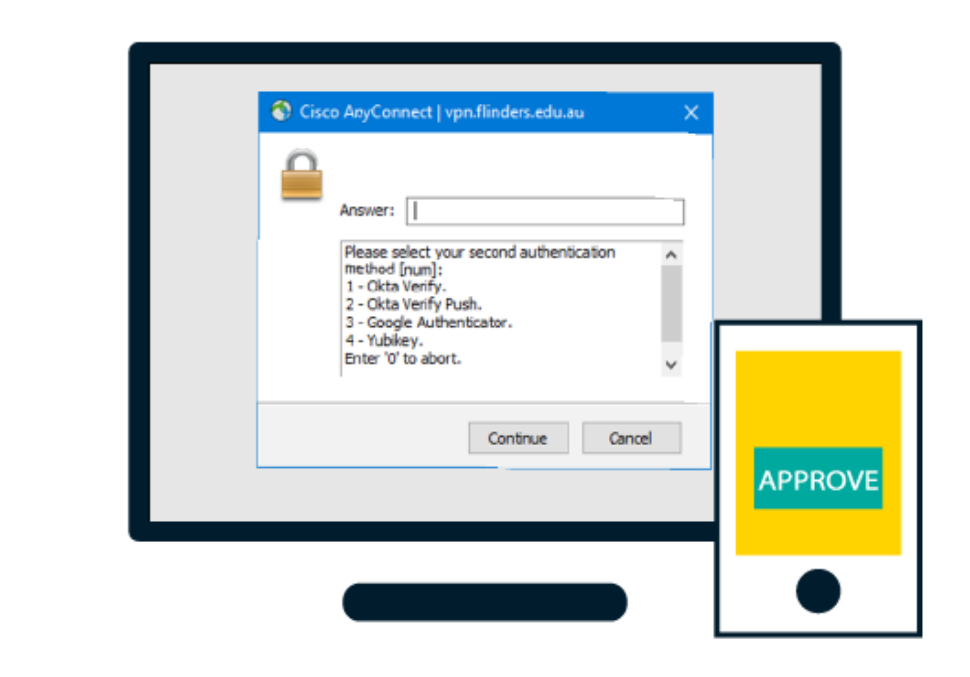
- Cisco AnyConnect Secure Mobility Client Secure VPN access for remote workers For organizations of all sizes that need to protect sensitive data at scale, Duo is the user-friendly zero-trust security platform for all users, all devices and all applications.
- Custom TOTP Authentication
- Okta Cisco Vpn Saml
- Okta Demo Using Cisco VPN - YouTube
- Configure The Cisco ASA Gateway | Okta
Make sure you add a Group URL in Cisco AnyConnect settings that corresponds to the ASA server and group you use. If you are using Cisco ASDM utility, you can do this under Connection Profiles Your group Advanced settings Group Alias/Group URL.
Custom TOTP Authentication
About Okta Mobility Management
- The OMM menu is available only to orgs that implement Okta Mobility Management (OMM).
- Operations documented in this article are available only to customers who have already purchased OMM for their organization. New OMM sales are not supported. For more information, contact Okta Support.
This is an Early Access feature. To enable it, please contact Okta Support.
Okta Mobility Management (OMM) can provision password-based, device-wide VPN configurations directly to devices without requiring IT to duplicate infrastructures or implement application proxies and gateways. Okta uses the native VPN capabilities built into the mobile operating system to leverage existing VPN solutions and enable easy access to on-premises resources. Notes:.
- The OMM menu is available only to orgs that implement Okta Mobility Management (OMM).
- Currently, this feature is available only for iOS devices.
- Go to OMM > VPN.
- Click Add Device VPN.
- Select a VPN client.
Support Announcement: Apple no longer supports PPTP or Juniper VPN options. This is an Apple limitation.
Okta Cisco Vpn Saml
- Configure your VPN client as described in one of the following procedures:Configuring Cisco AnyConnect
- Under General Settings, consider the following:
- Application Label: The label displayed under the app on your home page. By default this is Cisco AnyConnect VPN.
- VPN Server: Enter the IP address or hostname of your VPN server. If you are using ipsec, you must specify the corresponding protocol. For example: ipsec://asa-gateway.example.com.
- Click Next.
- Under Sign-On Options:
- VPN Password: Select either:
- Delegated Authentication: Select this option if your company VPN is configured to authenticate with Active Directory and your Okta users are authenticated using AD Delegated Authentication. Choosing this setting specifies that you are using your AD credentials for VPN as well. This way Okta never persists your AD credentials in Okta, but allows you to update VPN profiles with those credentials on your end users' devices.
- Password Required: Select either:
- Administrator sets username, password is same as user’s Okta Password. Select this option if you want the VPN profiles to remain synced on the device with their Okta Password whether or not you are using Delegated Authentication.
- Administrator sets username, user sets password. Select this option if you do not want to tie the VPN password with the Okta or AD password. Okta pushes the VPN profiles/configs to the device without including a password, and the user can enter it on their device.
- Advanced Sign-On Settings. Optional.
- Group for authenticating connection: Specify the group policy name.
- Make sure you add a Group URL in Cisco AnyConnect settings that corresponds to the ASA server and group you use.
- If you are using Cisco ASDM utility, you can do this under Connection Profiles > Your group > Advanced settings > Group Alias/Group URL. For example: ipsec://asa-gateway.example/com/group1
- VPN Username.
- VPN username format: Use the drop-down menu to select a format.
- Password reveal: Check this if you want your users to securely see their password.
- This is how we determine what username to use in the VPN profile, this function the same way as the username mappings in other non VPN applications.
- Group for authenticating connection: Specify the group policy name.
- Click Done.
- In the People tab, assign your app to users and groups. You also need to make the app available to your end users via the Okta Mobile App Store (Android and iOS). To do so:
- Click to the Mobile tab.
- Click the Edit (pencil) icon and select the following:
- Prompt users to install the app on enrollment (iOS 7+)
- If a user already has the app, enable them to make it a managed app from the company app store (iOS 9+)
- Make this app available to users
Configuring Juniper SSL VPN- Select the Juniper SSL VPN option.
Support Announcement: Apple no longer supports Juniper VPN options on macOS Sierra. This is an Apple limitation. Okta will maintain this option, but will not support it with bug fixes.
- Under General Settings:
- Application Label: The label displayed under the app on your home page. By default this is populated by Juniper SSL VPN.
- Server: Enter the IP address of the Juniper VPN server.
- Click Next.
- Under Sign-On Options:
- VPN Password: Select either:
- Delegated Authentication: This setting is to be used if your company VPN is configured to authenticate with Active Directory and your Okta users are authenticated using AD Delegated Authentication. Choosing this setting specifies that you are using your AD credentials for VPN as well. This way Okta never persists your AD credentials in Okta, but allows you to update VPN profiles with those credentials on your end users devices.
- Password Required: Select either:
- Administrator sets username, password is same as user’s Okta Password. Select this option if you want the VPN profiles to remain synced on the device with their Okta Password whether or not you are using Delegated Authentication.
- Administrator sets username, user sets password. Select this option if you do not want to tie the VPN password with Okta or AD password. Okta pushes the VPN profiles/configs to the device without including a password, and the user can enter it on their device.
- Advanced Sign-On Settings. Optional.
- Realm: Specify a realm for authenticating the connection.
- Role: Specify a role for authenticating the connection.
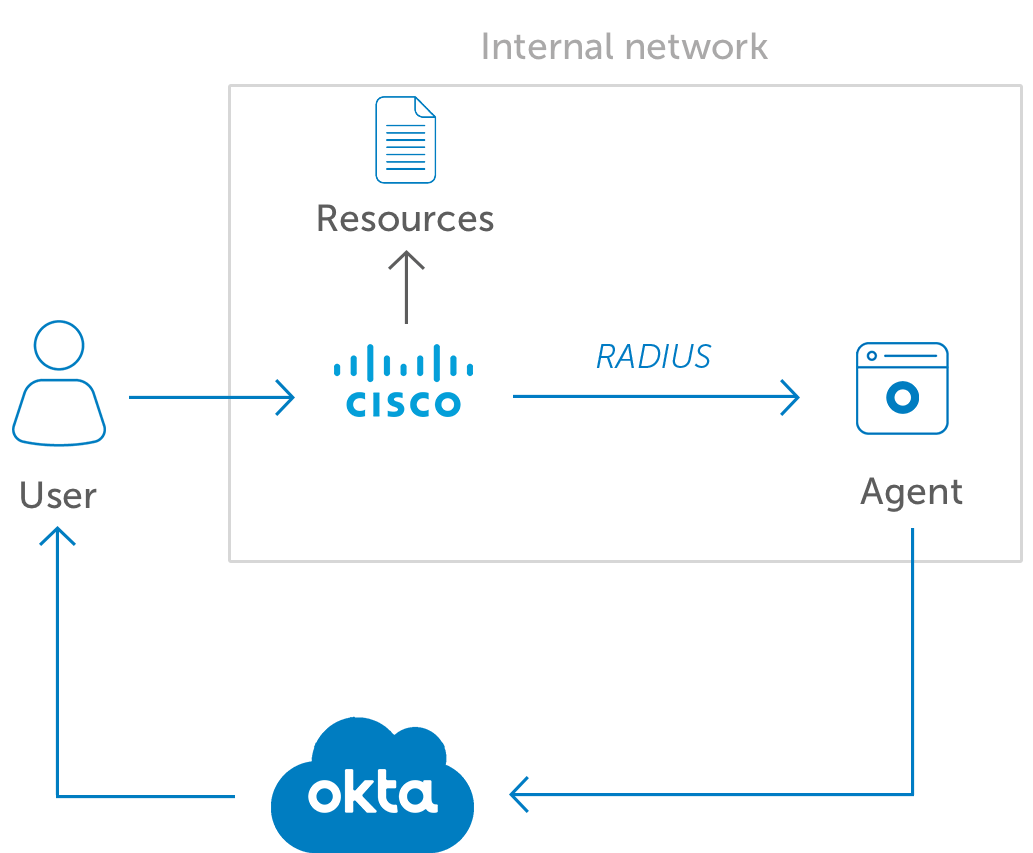
- RADIUS Authentication Behavior: Retaining this default button allows Okta to perform primary authentication.
- RADIUS Client
- UDP Port: Each RADIUS app has a unique number. Enter it in this required field.
- Secret Key: In this required field, enter the secret key that will be used to encrypt and decrypt the user password. This key must be identical to what is configured on the VPN server.
- VPN Username
- VPN username format: Use the drop-down menu to select a format.
- Password reveal: Check this if you want your users to securely see their password.
This allows Okta to determine which username to use in the VPN profile. This functions the same way as the username mappings in other non-VPN applications.
- Click Done.
This new, configured Juniper SSL VPN client now appears on the Device VPN page. Note that it is activated automatically.
Configuring L2TP VPN- Select the L2TP VPN option.
Support Announcement: Please note that Apple no longer supports PPTP. This is an Apple limitation.
- Under General Settings:
- Application Label: This is the label displayed under the app on your home page.
- Server: Enter the IP address or hostname of your VPN server. If you are using ipsec, the corresponding protocol must be specified, for example: ipsec://asa-gateway.example.com.
- Click Next.
- Sign-On Options. Here you choose how users sign in to the VPN. They can either use a password or they can sign in using Delegated Authentication if it is configured:
Advanced Sign On Settings:
- Shared Secret (L2TP only): Enter a shared secret key for VPN login.
VPN Password: Select either:
Delegated Authentication: This setting is to be used if your company VPN is set up to authenticate with Active Directory, and your Okta users are authenticated using AD Delegated Authentication. Choosing this setting specifies that you are using your active directory credentials for VPN as well. This way Okta never persists your AD credentials in Okta, but allows you to update VPN profiles with those credentials on your end users devices.
Password Required: Select either:
- Administrator sets username, password is same as user’s Okta Password. Select this option if you want the VPN profiles to remain synced on the device with their Okta Password whether or not you are using Delegated Authentication.
- Administrator sets username, user sets password. Select this option if you do not want to tie the VPN password with Okta or AD password. Okta pushes the VPN profiles/configs to the device without including a password, and the user can enter it on their device.
VPN Username.
- VPN username format: Use the dropdown menu to select a format. This is how we determine what username to use in the VPN profile, this function the same way as the username mappings in other non-VPN applications.
- Password Reveal: Check this if you want your users to securely see their password.
- Click Done.
Configuring Pulse Secure- Select the Pulse Secure VPN option. The Pulse Secure VPN configuration page opens.
- Under General Settings:
- Application Label: This is the label displayed under the app on your home page. By default this is populated by Pulse Secure VPN, but you can edit it if you wish.
- Server: Enter the IP address of the Pulse Secure VPN server.
Click Next.
- Under Sign-On Options:
- VPN Password: Select either:
- Delegated Authentication: This setting is to be used if your company VPN is set up to authenticate with Active Directory, and your Okta users are authenticated using AD Delegated Authentication. Choosing this setting specifies that you are using your AD credentials for VPN as well. This way Okta never persists your AD credentials in Okta, but allows you to update VPN profiles with those credentials on your end users devices.
- Password Required: Select either:
- Administrator sets username, password is same as user’s Okta Password. Select this option if you want the VPN profiles to remain synced on the device with their Okta Password whether or not you are using Delegated Authentication.
- Administrator sets username, user sets password. Select this option if you do not want to tie the VPN password with Okta or AD password. Okta pushes the VPN profiles/configs to the device without including a password, and the user can enter it on their device.
- Advanced Sign-On Settings. Optional.
- Realm: Specify a realm for authenticating the connection.
- Role: Specify a role for authenticating the connection.
This is how we determine what username to use in the VPN profile, this functions the same way as the username mappings in other non-VPN applications.
- VPN Username
- VPN username format: Use the dropdown menu to select a format. This is how we determine what username to use in the VPN profile, this function the same way as the username mappings in other non-VPN applications.
- Password Reveal: Check this if you want your users to securely see their password.
- Click Done.
In the People tab, assign your app to users and groups.
You will also need to make the app available to your end users via the Okta Mobile App Store. (Android and iOS). To do so
- Click to the Mobile tab.
- Click Edit and complete the following:
- Prompt end users who have already installed an iOS mobile app on their own to allow their admin to manage the app. (iOS only)
- Prompt users to install the app on enrollment. (iOS only)
- Deploy: Click the Make this app available to users check box.
- Under General Settings, consider the following:
Okta Demo Using Cisco VPN - YouTube
Once VPN configurations (profiles) and the respective VPN mobile apps are pushed to OMM-enrolled devices, users can sign in to VPN and work remotely.
Note: The way that VPN profiles are pushed depends on the VPN password settings you configured above:
Configure The Cisco ASA Gateway | Okta
- Delegated Authentication: VPN profiles are pushed when users are enrolled.
- User sets password: VPN profiles are pushed when users are enrolled, an app user is assigned, or a VPN app instance setting is changed.
- Password is same as Okta: VPN profiles are pushed when the user logs on.




